The general controls described in this section are divided into five broad categories:
- Authentication of users and limiting unauthorized access
- Hacking and other network break-ins
- Organizational structure
- Physical environment and physical security of the system
- Business continuity
Authentication of users is a process or procedure in an IT system to ensure that the person accessing the IT system is a valid and authorized user. Unauthorized users may be hackers or people within the company trying to gain access to data they are not entitled to. An IT system should require that users log in with a distinct user identification, or user ID, and a password.
Passwords should also be case-sensitive and changed every 90 days . The use of passwords can be strengthened by the use of a smart card. The smart card is a credit card–sized device with an integrated circuit that displays a constantly changing ID code. A newer technology to authenticate users is a security token, which plugs into the computer’s USB port and eliminates the need for a card reader.
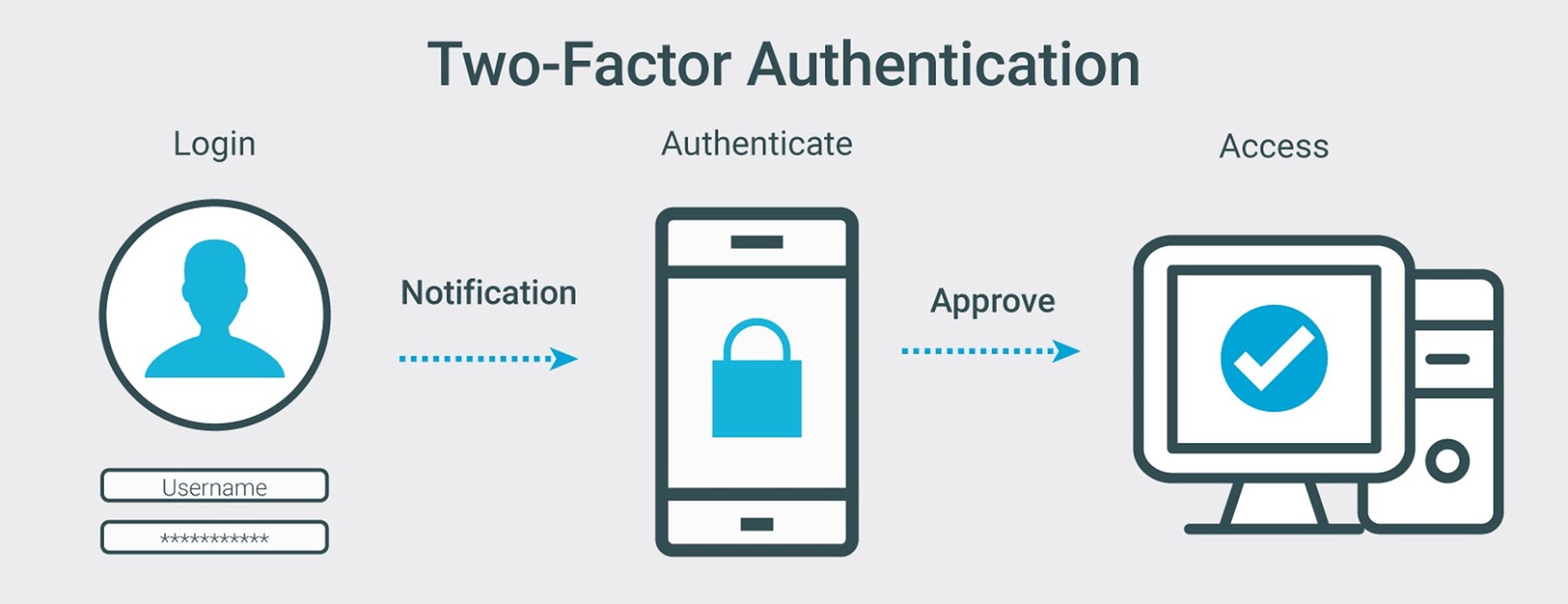
Two-factor authentication is based on something the user has, the token, and the password. The use of smart cards or tokens can reduce unauthorized access. When an authorized user logs in to a computer, a text to a smart phone includes a unique numeric code to enter to complete the log in. As an alternative, the smart phone app can be used for a “push” notification and approval.
Auto307