
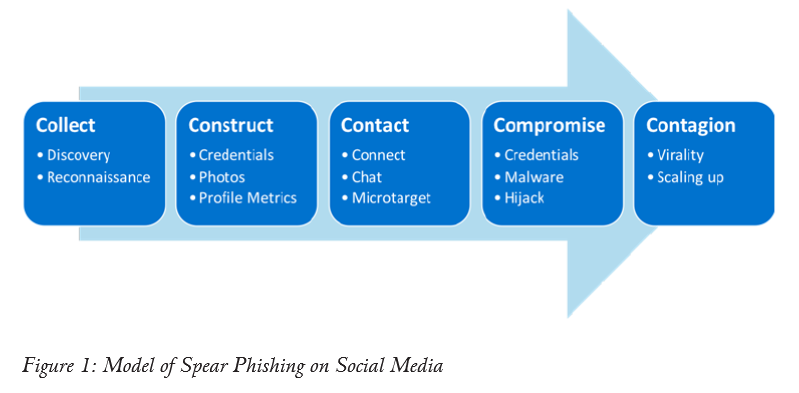
Spear phishing relies on social engineering to trick individuals into revealing sensitive information. While email remains the preferred medium to conduct spear-phishing attacks, social media has opened up new attack vectors for politically motivated cyberattacks. A theoretical model of spear phishing on social media is proposed and supported by recent empirical examples from the European Union and United States.
Auto172
Original
Bossetta, Michael. (2018). The Weaponization of Social Media: Spear Phishing and Cyberattacks on Democracy. Journal of international affairs. 70. 97-106.
State-sponsored cyber groups have long utilized spear phishing to pierce government networks. Spear phishing relies on social engineering to trick individuals into revealing sensitive information or downloading malicious software, rather than hacking into a system vulnerability by force. While email remains the preferred medium to conduct spear-phishing attacks, social media has opened up new attack vectors for politically motivated cyberattacks. Social media platforms, as high-trust environments typically accessed from a mobile device for personal entertainment or networking, are highly conducive waters for spear phishing. Moreover, the wealth of public information available on social media can be exploited by threat actors to devise sophisticated (and automated) spear phishing campaigns that target government and military personnel. This study examines how illiberal regimes are weaponizing social media to conduct spear phishing and cyber espionage against Western governments. A theoretical model of spear phishing on social media is proposed and supported by recent empirical examples from the European Union and United States. Much of the controversy around Russian interference in the 2016 U.S. election has focused on state-sponsored attempts to manipulate public opinion through social media. However, just weeks after President Donald J. Trump’s inauguration, Russian operatives demonstrated a cyber capability far exceeding the paid use of “trolls” to spread propaganda. More than 10,000 tweets-each laced with hyperlinks containing malware-were sent directly to U.S. Defense Department employees on Twitter. 1 The messages were tailored to appeal to the employees’ individual interests and generated click rates nearing 70 percent. In some cases, employees’ family members were targeted, and devices containing sensitive government information were compromised through shared home Wi-Fi networks. Zero FOX, a leading cybersecurity firm, referred to the malicious micro