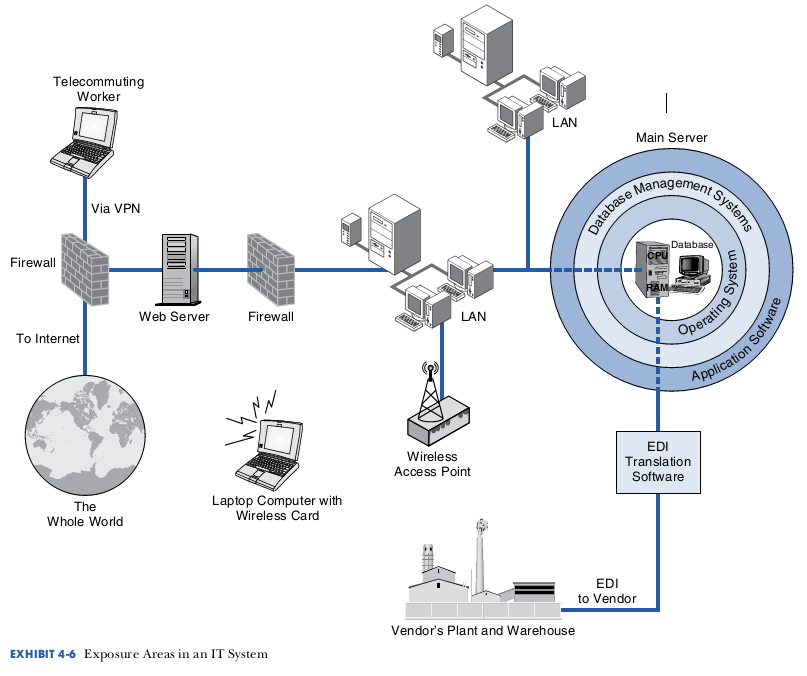
The existence of each of these components represents an exposure that should be controlled. These IT system exposures are entry points that make the organization susceptible to the IT risks described earlier.
The exposure areas are as follows:
- The operating system
- The database
- The database management system (DBMS)
- Local area networks (LANs)
- Wireless networks
- E-business conducted via the Internet
- Telecommuting workers and mobile workers
- Electronic data interchange (EDI)
- Application software
The first eight of these exposure areas can be controlled by the use of appropriate general controls such as those described in previous sections. The next eight sections give a brief description of each of the eight exposure areas. Some of these hardware or software components are described in more detail in other chapters. The ninth exposure area, application software, requires application controls. The description of application controls within application software is presented in the last section of this chapter. The purpose of the descriptions in this chapter is to provide only enough detail to allow an understanding of these exposures.
Auto318